
UNLE⛧SH THE BEAST ト何ゼ
| [MENU] | |||||||||
| [THOUGHTS] | [TECH RESOURCES] | [TRASH TALK] | |||||||
| [DANK MEMES] | [FEATURED ARTISTS] | [W] | |||||||
Rookie Challenge Unintended Solution
Nov. 2, 2020 // echel0n
Rookie

We played STMCTF'20 last weekend. In my opinion, this was the least enjoyable STMCTF. There were nice challenges but the overall quality was mehhhhhhhhh. Anyway, This is a writeup of third challenge of Reverse Engineering category. This is not an intended solution. I learnt this after got the flag.
The Action
The given files are private key and rookie-server executable.
- $ file rookie-server
- rookie-server: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=5b25dd40514f0f9b9f0beb41df1dfb8d5d1b9e48, for GNU/Linux 3.2.0, stripped
@icecream coded a client for this server, this is the client code.
- import os
- import sys
-
- with open("channel", "wb") as channel:
- channel.write(sys.stdin.buffer.read(512))
- os.system("openssl rsautl -decrypt -in channel -inkey ./private.pem")
-
- while True:
- with open("channel", "wb") as channel:
- channel.write(sys.stdin.buffer.read(1024))
- os.system("openssl rsautl -decrypt -in channel -inkey ./private.pem")
You can use this python code with this line below.
- nc 10.0.0.0 1337 | python client.py
I won't explain steps of reversing this executable, I will show you the code.
You should see something like this.
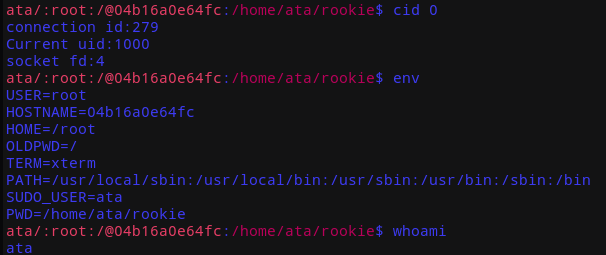
Umm WHAT?
At this point, I started to feel that this challenge environment is really messed up.
(Custom environment variables, custom privilege implementation for clients etc.)
Also the source code is in src/ we can use grep command to get small pieces of source code. Examples are;
- #include <fstream>
- #include "auth.h"
- #include <grp.h>
-
- //if session uid is 0, elevate, read the flag with 600:root permissions, and output it
- int yield_flag(session s){
- if(s.uid) return 1;
- setuid(0);
- std::ifstream flag("flag.txt");
- char buf[59];
- if (flag.is_open()){
- flag.read(buf,58);
- buf[58]=0;
- outputEncryptedString(buf);
- }
- flag.close();
- //exit(1337);
- }
-
- int authenticate(session s, char* password){
- std::string pwd(password);
- std::string hash = sha512(pwd);
- //outputEncryptedString((char*)hash.c_str());
-
- if(!s.uid || !hash.compare("8b586bf1b19e2d37191f780286c5ff74f7134ab650aebf7b6226d0d03b5d23acc0f443445315fb9f89ce2322fe1499d1124ca22f0be158ad7a8bb9ea549bb1ad")){
- outputEncryptedString("Authenticated\n");
- s.uid=0;
- setuid(0);
- yield_flag(s);
-
- }else{
- //Seriously.
- outputEncryptedString("Thats sha512. Its 17 characters [!-~]. Please don't waste your time bruteforcing. You can't.\n");
- }
- }
-
- int dropPrivs(){
- /*
- Set uid and gid to 1000, dropping root privileges.
- */
-
- /* If root privileges are to be dropped, be sure to pare down the ancillary
- * groups for the process before doing anything else because the setgroups( )
- * system call requires root privileges. Drop ancillary groups regardless of
- * whether privileges are being dropped temporarily or permanently.
- */
- gid_t guid = 1000;
- setgroups(1, &guid);
- setgid(guid);
- setuid(0);
- seteuid(1000);
-
- }
- int builtin_exit(session s, char ** args) {
- //...
- //check against hash
- return 0;
- }
-
- int builtin_cd(session s, char ** args) {
- if (args[1] == NULL) {
- outputEncryptedString((char*)"No arguement to \"cd\"\r\n");
- } else {
- if (chdir(args[1]) != 0) {
- outputEncryptedString((char*)"No such directory\n");
- }else{
- outputEncryptedString((char*)" \n");
- }
- }
- return 1;
- }
-
- int builtin_flag(session s, char ** args) {
- if(s.uid)
- outputEncryptedString((char*)"STMCTF{You need to elevate for flag}\r\n");
- else yield_flag(s);
- }
-
- int builtin_authenticate(session s, char ** args) {
- char* passwd = args[1];
- authenticate(s,passwd);
- }
-
- int builtin_cid(session s, char ** args) {
- char* passwd = args[1];
- sprintf (buffer, "connection id:%d\nCurrent uid:%d\nsocket fd:%d\n", s.connectId, s.uid, s.sockfd);
- outputEncryptedString(buffer);
- }
-
- int builtin_sudo(session s, char ** args) {
- char* command = args[1];
- if(args[0]==0) return 1;
-
-
- if(s.uid==0 && !strcmp(args[1],"cid")){
- builtin_cid(s, &args[1]);
- }
- else if(s.uid==0 && !strcmp(args[1],"stm")){
- builtin_flag(s, &args[1]);
- }
- else if(s.uid==0 && !strcmp(args[1],"cd")){
- builtin_flag(s, &args[1]);
- }
- else if(s.uid=0 && !strcmp(args[1],"exit")){
- outputEncryptedString("Not Allowed\n");
- }
- }
-
- int builtin_rf(session s, char ** args) {
- setuid(1000);
- std::ifstream fs(args[1]);
- char buf[512];
- if (fs.is_open()){
- while(!fs.eof()){
- fs.read(buf,512);
- std::cout << buf;
- }
- }
- fs.close();
- }
-
- int (*builtin_func[])(session, char **) = {&builtin_cd, &builtin_cid, &builtin_sudo, &builtin_exit, &builtin_authenticate, &builtin_flag, &builtin_rf};
-
- int numBuiltins = 7;
-
- const char *builtin_str[] = {
- "cd",
- "cid",
- "sudo",
- "exit_BIND",
- "authenticate",
- "stm",
- "readfileplain"
- };
Main code is...
- int main(int argc, char *argv[]){
- #ifdef DEBUG
- std::cerr << "<WARNING> Running with debug enabled\n";
- #endif
-
- //register sigint handler
- signal(SIGINT, signalHandler); signal(SIGABRT, signalHandler); signal(SIGTERM, signalHandler);
- signal(SIGCHLD, SIG_IGN);
-
- char **args;
- int status;
- std::string str;
- char userbuf[64];
- char hostbuf[64];
- char cwd[128];
- int portno;
- socklen_t clilen;
- struct sockaddr_in serv_addr, cli_addr;
- int n;
-
- if(argc!=2){
- portno = 4444;
-
- if(argc!=2){
- portno = 4444;
- return 1;
- }else{
- portno = atoi(argv[1]);
- }
-
-
- //create file descriptor
- sockfd = socket(AF_INET, SOCK_STREAM, 0);
- if (sockfd < 0) return 2;
-
- serv_addr.sin_family = AF_INET;
- serv_addr.sin_addr.s_addr = INADDR_ANY;
- serv_addr.sin_port = htons(portno);
- serv_addr.sin_port = htons(portno);
- clilen = sizeof(cli_addr);
-
-
-
- int connectionID = 0;
- //bind to tcp port
- if (bind(sockfd, (struct sockaddr *) &serv_addr,sizeof(serv_addr)) < 0)
- return 3;
-
- listen(sockfd,5);
- int newsockfd;
- while(newsockfd = accept(sockfd,(struct sockaddr *) &cli_addr,&clilen)){
- char cliIP[16];
- std::cout << "Accepted connection from " << inet_ntoa(cli_addr.sin_addr) << "\n";
-
-
- session s;
- s.connectId=connectionID++;
- s.sockfd=newsockfd;
- s.uid=1000;
-
-
- if(!pid){
- initSession(s, newsockfd, serv_addr);
- }
- //close only for parent so we don't exceed the fd limit 1024. Socket is alive for child fork.
- close(newsockfd);
- }
- }
It goes like this, we got what we have to know from here.
Actually we have root privileges but the server is telling lies about our UID.
Also, it seems, the intended way to solve this challenge running stm command.
WE ARE ALREADY ROOT, WHY WE HAVE TO CHASE AFTER THIS STM COMMAND ????
Yeah, why?
We just have to bypass argc checks and we can run actual 'bash' commands by root.
And the answer was the 'bash' command itself.
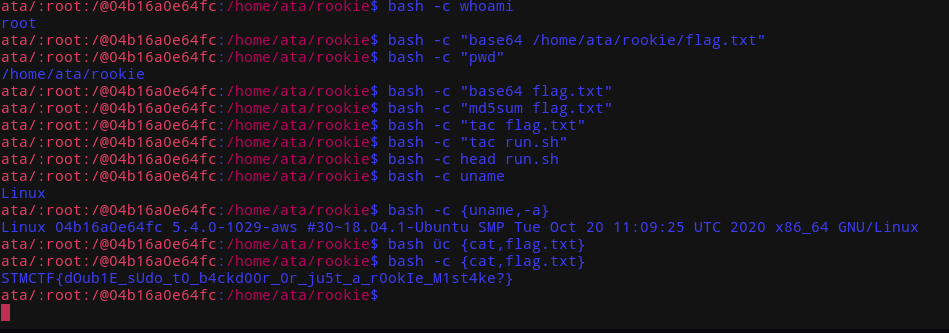
The flag is STMCTF{dOub1E_sUdo_t0_b4ckd00r_0r_ju5t_a_r0okIe_M1st4ke?}
At this point, I was like 'What, which double sudo?'. I thought that was the intended solution.
Real solution was 'sudo sudo stm'.