
UNLE⛧SH THE BEAST ト何ゼ
| [MENU] | |||||||||
| [THOUGHTS] | [TECH RESOURCES] | [TRASH TALK] | |||||||
| [DANK MEMES] | [FEATURED ARTISTS] | [W] | |||||||
Decrypt configuration files like exactly how Huawei ONT does
July 28, 2021 // echel0n
Huawei's aescrypt2 emulation with Qiling Framework
Hello guys! In this blog i will show you how to decrypt Huawei ONT configuration files like exactly how the device handle operations of encryption/decryption. TLDR version is at the end.
aescrypt2
The binary is well-known and already reverse-engineered to death. It has also an alternative version to encrypt/decrypt files (ex: hw_ctree.xml) on your computer
palmerc's AESCrypt2 tool
I wanted more natural solution because the device's filesystem was there and the original aescrypt2 also was there then i thought it could be great exercise for emulating with qiling framework. By the way, while i was working on this binary, I did my first contribution to an open-source project, i've implemented 2 syscalls. (go me!) All work done in Huawei OptiXstar HG8245X6. I wont explain the steps of obtaining the needed files. It is a different story.
Lazy Man's Work
Actually, i did not analyze the binary file with r2 or cutter for even once. I just checked how the device calls that binary and found some examples like below.
- $ grep -R aescrypt2
- .
- .
- .
- bin/restorehwmode.sh: $var_pack_temp_dir/aescrypt2 0 $2 $2"_tmp"
- bin/restorehwmode.sh: $var_pack_temp_dir/aescrypt2 1 $1 $1"_tmp"
- .
- .
Then I checked the lines in scripts that uses aescrypt2.
- HW_Script_Encrypt()
- {
- if [ $1 -eq 1 ]
- then
- gzip -f $2
- mv $2".gz" $2
- $var_pack_temp_dir/aescrypt2 0 $2 $2"_tmp"
- fi
- }
- ...
- ...
- ...
- # decrypt var_ctree
- $var_pack_temp_dir/aescrypt2 1 $1 $1"_tmp"
- if [ 0 -ne $? ]
- then
- echo $1" Is not Encrypted!" >> $var_upgrade_log
- else
- echo $1" Is Encrypted!" >> $var_upgrade_log
- varIsXmlEncrypted=1
- mv $1 $1".gz"
- gunzip -f $1".gz"
- fi
- ...
- ...
- ...
I understood how encryption and decryption operations work quickly, it explains itself. When encryption is needed, first it will be zipped then it will be encrypted. Cha cha real smooth Huawei! They answered the legendary job interview "Is it better to encrypt before compression or vice versa?" question. It may work but only when the keys are not lying around and not plaintext. (The key in-use is in /etc/wap/aes_string) (It's okay tho)
The Action
My strategy was a mess. Firstly, I just copied all filesystem including /dev and /proc directories to make it feel like in home. Literally, i didn't do a proper static analysis of it even no readelf or objdump. I just fired Qiling() class with suitable arguments.
- def prepare() -> Qiling:
- #
- # decrypt var_ctree
- # var_pack_temp_dir=/bin/
- # var_default_ctree=/mnt/jffs2/customize_xml/hw_default_ctree.xml
- # var_temp_ctree=/mnt/jffs2/customize_xml/hw_default_ctree_tem.xml
- # $var_pack_temp_dir/aescrypt2 1 $var_default_ctree $var_temp_ctree
-
- cur_dir = os.path.abspath(".")
- ql = Qiling(
- [
- cur_dir + "/rootfs/bin/aescrypt2",
- "1", # decrypt flag for encryption set to 0
- "/mnt/jffs2/hw_ctree.xml", # encrypted file
- # i couldnt understand what second arg's purpose because
- # aescrypt2 renames this field to original file
- # it is like a dummy file imo.
- "/tmp/hw_ctree.gz",
- ],
- cur_dir + "/rootfs/",
- verbose=QL_VERBOSE.DEBUG,
- console=True,
- )
- return ql
I literally was waiting to qiling could do the rest magically. I was wrong and started to pay attention to details. The first problem was readv syscall was not implemented, i worked to implement it properly. It was not that hard, checked the man pages to know how it operates.
- def ql_syscall_readv(ql, fd, vec, vlen, *args, **kw):
- # it is like read() but reads into more than one buffer.
- # if you use dev branch while using qiling you already have it.
- regreturn = 0
- size_t_len = ql.pointersize
- iov = ql.mem.read(vec, vlen * size_t_len * 2)
- ql.log.debug("readv() CONTENT:")
-
- for i in range(vlen):
- addr = ql.unpack(
- iov[i * size_t_len * 2 : i * size_t_len * 2 + size_t_len]
- )
- l = ql.unpack(
- iov[
- i * size_t_len * 2
- + size_t_len : i * size_t_len * 2
- + size_t_len * 2
- ]
- )
- regreturn += l
- if hasattr(ql.os.fd[fd], "read"):
- data = ql.os.fd[fd].read(l)
- ql.log.debug(data)
- ql.mem.write(addr, data)
-
- return regreturn
I wish I could say i've set this syscall then it worked but another problem was occured after this one.
- [+] 0x04814230: readv(fd = 0x6, vec = 0x7ff3bb04, vlen = 0x2) = 0xdff
- [+] [+] Received Interupt: 2 Hooked Interupt: 2
- [x]
- Traceback (most recent call last):
- File "/usr/lib/python3.9/site-packages/qiling/os/posix/posix.py", line 184, in load_syscall
- retval = syscall_hook(self.ql, *params)
- File "/usr/lib/python3.9/site-packages/qiling/os/posix/syscall/unistd.py", line 159, in ql_syscall__llseek
- ret = ql.os.fd[fd].lseek(offset, origin)
- File "/usr/lib/python3.9/site-packages/qiling/os/filestruct.py", line 46, in lseek
- return os.lseek(self.__fd, lseek_offset, lseek_origin)
- OverflowError: Python int too large to convert to C long
- [=] Syscall ERROR: ql_syscall__llseek DEBUG: Python int too large to convert to C long
As every professional does, immediately called print function with this value in that function. I found out this value actually was a negative number but the function assumes it is unsigned. Then i've implemented my _llseek syscall like this, i don't know if it is a proper patch but it worked for me.
- def ql_syscall__llseek(ql, fd, offset_high, offset_low, result, whence, *args, **kw):
-
- # _llseek negative seek bug fix
- offset_high = int.from_bytes(
- offset_high.to_bytes(ql.pointersize, "little"), "little", signed=True
- )
- offset_low = int.from_bytes(
- offset_low.to_bytes(ql.pointersize, "little"), "little", signed=True
- )
-
- offset = offset_high << 32 | offset_low
- origin = whence
- regreturn = 0
- try:
- ret = ql.os.fd[fd].lseek(offset, origin)
- except OSError:
- regreturn = -1
- if regreturn == 0:
- ql.mem.write(result, ql.pack64(ret))
- ql.log.debug(
- "_llseek(%d, 0x%x, 0x%x, 0x%x) = %d"
- % (fd, offset_high, offset_low, origin, regreturn)
- )
- return regreturn
After patching this call succesfully, I realized aescrypt2 reads first 8 bytes of given file, first 4 bytes are -if I understood correctly- file encryption type or smt like that and other 4 bytes are for checksum.
(I didn't analyze it, if something messed up while decrypting it, suprisingly it throws a checksum error, lol.)
Then i noticed that rename() syscall also was not implemented (it's implemented in dev branch now) then wrote it down too but it was not necessary because given file is already decrypted at that time.
The Euphoria
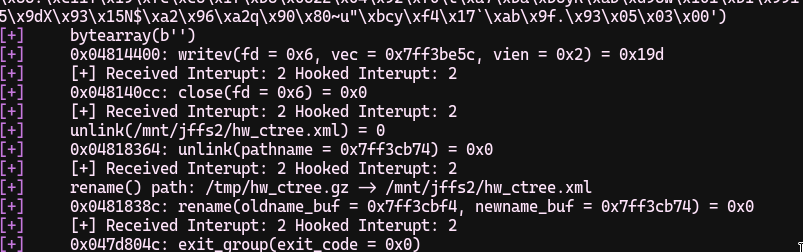
When it exited with exit code 0, i felt that. I quickly tried to gunzip it.
- $ mv hw_ctree.xml hw_ctree.gz
- $ gunzip -f hw_ctree.gz
- $ # when command is executed succesfully, i slammed my fist on the table
- $ cat hw_ctree
Too Long Didn't Read
I've done something unnecessary emulation while having aescrypt2 alternative tool and felt awesome and decided to brag about it.
Note: I created the needed file list from open call. In case of missing something, if you are able to pull all files(shared libraries, /proc/wap_proc and /dev included), get all of them. kmc_store_* files are not included in repository because i didnt analyze it, i dont know yet if it is unique file or not. kmc_store_* files are vital. if it is blank or random it will check another directories for backup. If it could not find any, it will throw this error;
- hw_ssp_ctool.c:934:HMAC check failed: wrong key, or file corrupted.
- Succesful decryption operation will open these files.
- /etc/ld-musl-arm.path,
- /lib/libhw_ssp_basic.so,
- /lib/libclang_rt.builtins_s.so,
- /lib/libunwind_s.so.1,
- /lib/librtos_musl_extend.so,
- /dev/hlp,
- /proc/wap_proc/proc_dbg,
- /lib/libpolarssl.so,
- /proc/wap_proc/wap_msg_group
- /mnt/jffs2/kmc_store_A3,
- /mnt/jffs2/kmc_store_A3,
- /mnt/jffs2/kmc_store_B3,
- /mnt/jffs2/kmc_store_B3,
- /mnt/jffs2/kmc_store_A,
- /mnt/jffs2/kmc_store_B,
- /var/ksf_check_done,
Although it was not necessary, i am happy to being able to do this way, it feels like, it is a more elegant way to accomplish this.
Full script is available in my having-fun-with-qiling repo.
Here
Bonus
I also saw another AES key in /bin/clid binary but i dont know which part of it is using the key and how. I am leaving it here. If you already know how and where this key is used please contact me on twitter @echel0n_1881
- Df7!ui%s9(lmV1L8