UNLE⛧SH THE BEAST ト何ゼ
| [MENU] | |||||||||
| [THOUGHTS] | [TECH RESOURCES] | [TRASH TALK] | |||||||
| [DANK MEMES] | [FEATURED ARTISTS] | [W] | |||||||
Analyzing shellcode with Qiling Framework
Dec. 23, 2020 // echel0n
Analyzing shellcode with Qiling Framework
Hello guys!
In this blog, i will show you how to analyze malicious shellcode with qiling framework.
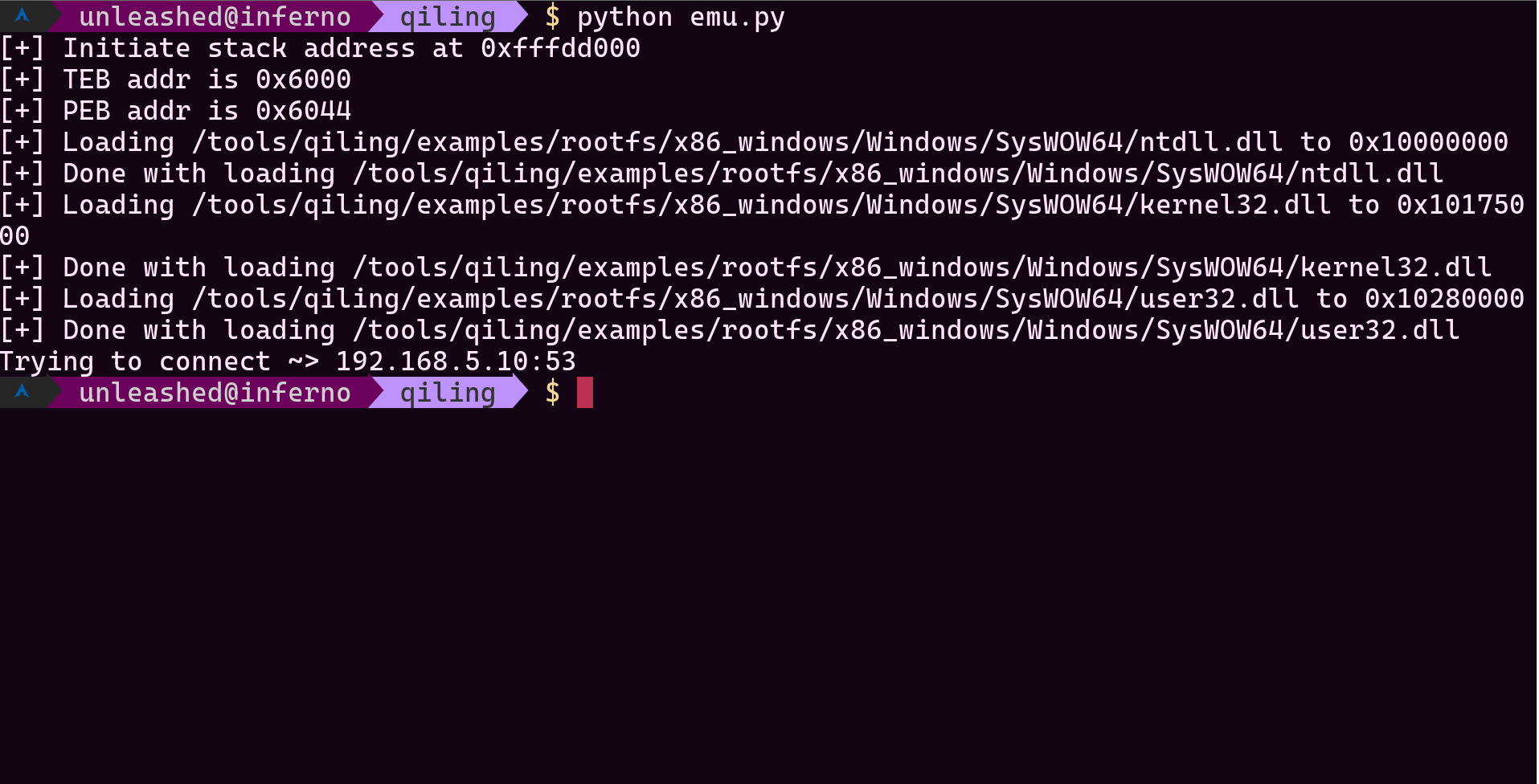
Actually, If you really need quick check if some shellcode is trying to connect any IP, you can use this example.
- #!/usr/bin/env python
- """
- This code will hook connect() function and will print out the address which
- shellcode is trying to.
- The sample shellcode is from BATTLEWARE CTF
- sample shellcode base64 encoded:
- kJCQkJCQkJCQkJCQkJCQkJCQkJDb3rpanC/h2XQk9F4zybFSMVYXg+78AwyPzRRMR5PXrJj0XkmpNAQamoROThduAnqsAouNBajtoJaBzqMU2AIDJBNXQmFOmhY6BAmGT1CSLQN0ktLUd7NFbi4TZKNaGn6gZ9T1EhPn32rcRB5DL5RnZNDjkZZt9GbkqXF8TjkhWG7utCt8W7JzYVoXCJ3Xlt4Xo7z6fHfcW9nW4buCh0ewL9P1mycQNCO4Pk9QiuH7/qZqIvnJQJKVN2vjvPM/s9bSP1gm2pXPdnRGsCY0Nlgsu2l4TxECE6ry7UyxCIaOuQxjBl9mm07IHwLLgr7Lwe+BQOYQT6GDAjhB3njvXvQUc8yT5PrtC7OrwEVRRnr8R5sax8NA38bKBVvt3NNkqYiLMmdmau3J0CRCgLSxqBPCveTlKg9RsFWgNTQu3KW75WTV8afNflwyTONf6ZMa3Bts2fxuaaW6gwO2LqOwtwc=
- """
-
- from qiling import *
- from qiling.const import *
- from binascii import hexlify
-
- # IP format for humans
- def ip_builder(IP: bytes) -> str:
- """TODO: Docstring for ip_builder.
- :IP: bytes
- :returns: str
- """
- first = int(IP[0:2], 16)
- second = int(IP[2:4], 16)
- third = int(IP[4:6], 16)
- fourth = int(IP[6:8], 16)
-
- return f"{first}.{second}.{third}.{fourth}"
-
-
- def human_readable_ip_str(name):
- ipp_addr_version = hexlify(name[0:2])
- ip_addr_port = int(hexlify(name[2:4]), 16)
- ip_addr = hexlify(name[4:8])
-
- ip = ip_builder(ip_addr)
-
- print(f"Trying to connect ~> {ip}:{ip_addr_port}")
-
-
- def _connect(ql, address, params):
- value = ql.mem.read(params["name"], params["namelen"])
- human_readable_ip_str(value)
-
-
- def prepare() -> Qiling:
-
- shellcode = open("./bin.sc", "rb").read()
- rootfs = "/tools/qiling/examples/rootfs/x86_windows"
- ostype = "windows"
- archtype = "x86"
- output = "default"
-
- ql = Qiling(
- shellcoder=shellcode,
- rootfs=rootfs,
- ostype=ostype,
- archtype=archtype,
- output=output,
- console=True,
- )
-
- ql.filter = ["connect"]
- ql.set_api("connect", _connect, QL_INTERCEPT.ENTER)
- return ql
-
-
- def main():
- ql = prepare()
- try:
- ql.run()
- except:
- pass
-
-
- if __name__ == "__main__":
- main()
Example output below;